- Content Antivirus (c,e,s-wall)
- The Antivirus Traditions
- There are two main approaches to virus deliverance.
- File Scanning allows detecting an infected file and possibly curing it. Unfortunately, it is the time consumption process especially in the case of large number of files. This process could be performed manually or by scheduler. In both cases, we concern with the long process, which could not be performed frequently.
- File Monitoring allows to catch open, read or write operations on all or selected files and to perform AV scan on the file being operated. It is more efficient technique allows scanning only files, which a program needs. However, as the result we should waste the time and CPU resources to scan the same file during each operation. If the files are big (database or multimedia files) or are used often the CPU will be overloaded. Of course, fine file monitor tuning could help but it requires tuning.
All hese strategies presume that the potentially infected files are already on your disk and already could hurt you. - x-Wall Technology
-
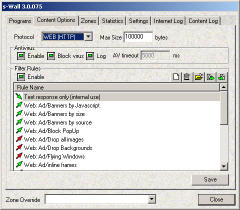 As the majority of the viruses are coming through the network, we should scan firstly the network traffic blocking viruses directly inside windows network subsystem. It could be performed transparently and independently for applications and the result viruses will not be passed to your disk. It saves the CPU resource and significantly decreases virus attack probability. As the majority of the viruses are coming through the network, we should scan firstly the network traffic blocking viruses directly inside windows network subsystem. It could be performed transparently and independently for applications and the result viruses will not be passed to your disk. It saves the CPU resource and significantly decreases virus attack probability. - There several AV controlling options
- Enable turns on/off antivirus behavior completely and separately for internet protocol (application type)
- Block virus switches between simple virus detecting and blocking. Do not disable virus blocking until you are sure that you need the content exposed like infected. If Block virus is on x-Wall prevents the infected internet content receiving and substitutes it with safe, detailed and suitable notification message.
- Log controls the appearance of AV events in Log tab and in Log file (if log is switched on in Settings tab)
- AV timeout parameter defines the maximum AV response time. As x-Wall fulfils AV checking directly in the network subsystem, it could be impossible to wait forever for AV engine response. Nevertheless, AV response time could vary depending on chosen AV system, CPU loading and complexity of processing content (ex: archive inside archive), the situation should be foreseen. AV timeout parameter limits "waiting for AV" time.
- The Content Substitution
-
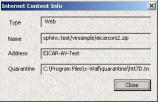 Here are the content substition samples appeared instead of infected e-mail or web page and the alert message Here are the content substition samples appeared instead of infected e-mail or web page and the alert message
x-Wall : Virus Alert
Virus Name EICAR-AV-Test
Content location sphinx.test/virsample/eicarcom2.zip
Quarantine
"C:\Program Files\x-Wall\quarantine\htt7D.tmp"
- Using
- x-Wall does not include an antivirus program, but can utilize some famous preinstalled antivirus processors. Choose suitable antivirus in Settings dialog.
- Some antivirus systems compatible to x-Wall can provide only file scanning. For that reason, the internet content should be temporarily saved on the disk as the files in x-Wall's quarantine for AV scan. It could interfere with AV's file monitoring (if any). Do not enable AV's file monitoring in the x-Wall's quarantine directory ("C:\Program Files\x-Wall\quarantine").
|
 As the majority of the viruses are coming through the network, we should scan firstly the network traffic blocking viruses directly inside windows network subsystem. It could be performed transparently and independently for applications and the result viruses will not be passed to your disk. It saves the CPU resource and significantly decreases virus attack probability.
As the majority of the viruses are coming through the network, we should scan firstly the network traffic blocking viruses directly inside windows network subsystem. It could be performed transparently and independently for applications and the result viruses will not be passed to your disk. It saves the CPU resource and significantly decreases virus attack probability.  Here are the content substition samples appeared instead of infected e-mail or web page and the alert message
Here are the content substition samples appeared instead of infected e-mail or web page and the alert message